New type of attack uses the features of Chrome on Android phones, which hide the address bar when the user scrolls the page down. The address will reappear when you scroll the page up. An attacker can exploit this feature and force the browser to hide the original address bar and instead display its own, …
Continue reading Be careful with Chrome on your Android phone
Category:Blog
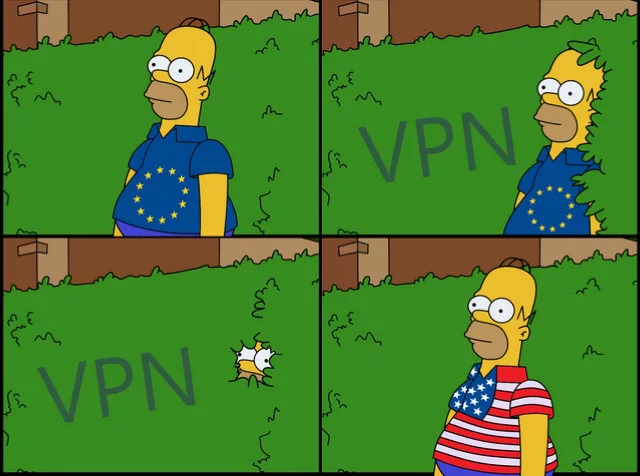
VPN – Protecting Your Communication and Salvation for the European Internet?
In connection with the adoption of the new European legislation known as Article 13/17, which introduces new regulations for Internet content providers, more talks about VPN have become a tool that will allow the Internet to continue to be used without restriction in Europe How can it help not only in finding content on the …
Continue reading VPN – Protecting Your Communication and Salvation for the European Internet?
WordPress – admin account for an attacker!
If you use WordPress for your website, make sure you have at least 5.1.1 version – the version number is on all pages in the administration at the bottom right or on the Dashboard in the “At a glance” box. If your WordPress is older, update to the latest version . Simon Scannell on the …
Continue reading WordPress – admin account for an attacker!
Unhackable car alarm
According to their creators, Troy was impregnable, Titanic was unsinkable, and Pandora’s car alarm was unhackable. However, someone (or something) appears to be brave enough to accomplish the impossible. The Pandora and Viper products were tested by Pen Test Partners and found that with these alarms the car is even more vulnerable than without them. …
Continue reading Unhackable car alarm
Brute-force attack – demo
Jak funguje tzv. brute-force útok? Můžete si ho vyzkoušet.
How long it can take to crack your password?
Calculation of time needed to crack password via brute-force attack.
Message encryption – demo
Plain (email) Client to Server (Facebook Messenger, Gmail) End to end (Signal, Threema, Wire) You Hello there! Send Key: Transfer to server (internet): Hacker Server: AdminPolice Transfer to receiver (internet): Hacker Receiver: Key:
Studie odhalila možné útoky na “bezpečné” messengery
12. 12. 2018 Vitor Ventura zveřejnil na blogu výsledky studie Cisco Talos, která se zaměřila na tři aplikace pro posílání zpráv – Signal, Whatsapp a Telegram.
Try the simple hacker’s trick
One of the attackers’ goals is to deceive the user in such a way that he runs a malicious program on his own computer. Today, most common users know that opening exe files that come as an attachment in an email or downloaded from the Internet is not very safe. That’s why hackers try to …
Continue reading Try the simple hacker’s trick
Uživatel Linuxu s vysokým UID může získat vyšší oprávnění
Chyby se samozřejmě nevyhnou ani Linuxu. Pokud například administrátor přiřadí neprivilegovanému uživateli UID vyšší než 2147483647 (vyšší než INT_MAX), může tento uživatel spouštět jakýkoliv příkaz systemctl. Což pravděpodobně administrátor nezamýšlel 🙂 Rich Mirch zveřejnil proof-of-concept (PoC) exploit pro uživatele s UID 4000000000 Chyba dostala přiřazeno CVE-2018-19788.